Email is the starting point for 94% of cyberattacks.

Why is email
security important?
Email security is crucial due to its central role in business communication. With a staggering 333 billion emails exchanged daily and employees receiving an average of 120 emails per day, it’s a prime target for cybercriminals. They employ tactics like business email compromise, malware, and phishing campaigns, leading to significant financial, data, and reputational setbacks.
Our Email Security Services
Advanced Threat Detection
Proactive scanning for sophisticated threats, including phishing attacks, malware, and ransomware.
Email Encryption
Secure your sensitive data with robust email encryption, ensuring confidential information remains private.
Spam Filtering
Efficient filtering mechanisms to weed out spam and malicious content, keeping your inbox clean and secure.
User Training & Awareness
Empower your team with comprehensive training to recognize and avoid email-based threats, enhancing overall security awareness.
Common Business Email Threats
Data Exfiltration
Data exfiltration involves the unauthorized transfer of data from an organization, either through manual actions or malicious programming. Email gateways play a crucial role in preventing businesses from unintentionally sending sensitive data, thereby averting potentially costly data breaches.
Spam
Spam refers to the bulk sending of unsolicited messages without the recipient’s consent. While businesses may use spam emails for commercial purposes, scammers exploit spam to disseminate malware, deceive recipients into revealing sensitive information, or extort money.
Malware
Malware, a condensed form of malicious software, is designed to harm or disrupt computers and computer systems. It encompasses various threats such as viruses, worms, ransomware, and spyware.
Impersonation
Impersonation occurs when cybercriminals masquerade as a trusted person or organization to illicitly obtain money or data via email. Business email compromise (BEC) is a prime example, where scammers impersonate an employee to pilfer from the company, its customers, or its partners.
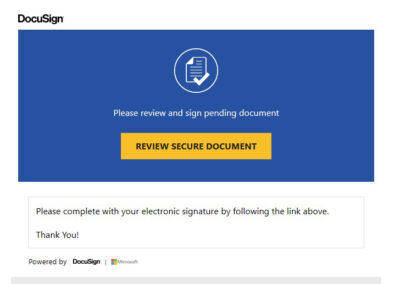
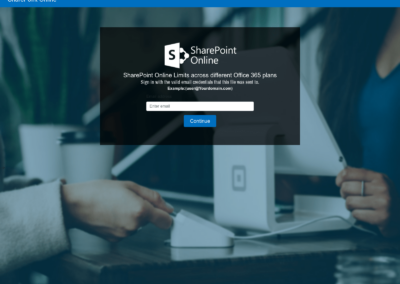
Phishing
Phishing is the deceptive practice of posing as a trustworthy entity to trick victims into divulging valuable information, such as login credentials and sensitive data. Variants of phishing include spear phishing, vishing, and whaling.
The Phishing Epidemic
Spam and phishing emails have reached alarming levels. Cybercriminals have been exploiting AI technology to create deceptive messages that are highly convincing and difficult to identify as fraudulent. These attacks pose a significant risk to your business, potentially leading to data breaches, financial losses, and reputational damage.
Partner with Synchroworks for
Your Sophos Email Security Solution
Synchroworks is committed to helping you safeguard your business against the rise of email threats.
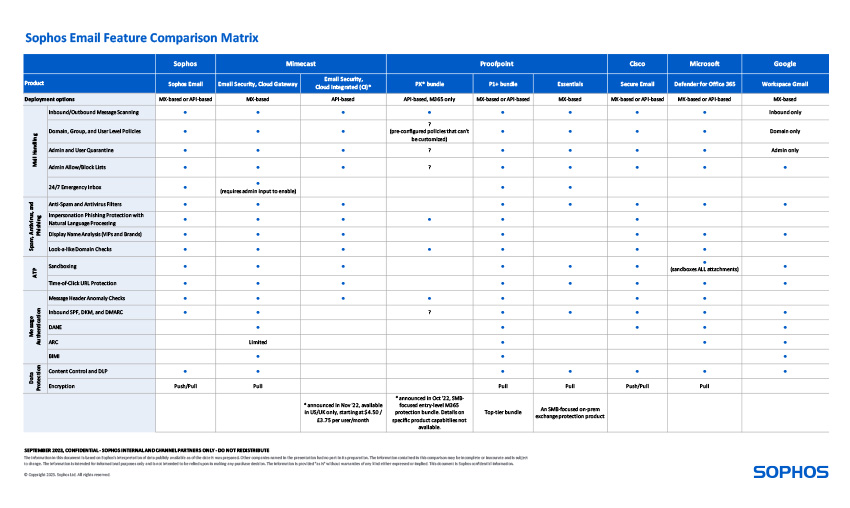
Email Protection Features
As email threats continue to advance in complexity, organizations must establish robust email security systems to safeguard their data, reputation, and financial well-being. Businesses should opt for secure email solutions that provide comprehensive threat protection across applications, devices, email platforms, identities, data, and cloud workloads.
Keep Threats Out
Sophos’ cloud sandbox thoroughly examines file processes, file activity, registry activity, and network connections to proactively prevent ransomware and various other types of malware.
Let Trusted Senders In
Sophos Email conducts real-time scans of all incoming messages, utilizing SPF, DKIM, and DMARC authentication techniques to identify crucial phishing indicators like brand spoofing and impersonation attempts. It detects and prevents phishing emails before they can reach your users.
Deep AI Learning
Sophos employs deep learning artificial intelligence to swiftly thwart zero-day malware and undesired applications.
Encrypt & Authenticate
Encrypt your messages by incorporating a digital signature for sender verification through S/MIME or choose from a range of customizable encryption options such as TLS encryption, attachment and message encryption (PDF and Office), or opt for comprehensive web portal encryption.
Explore Additional Services

Voice Solutions
Revolutionize your business communication with advanced voice technologies

Pen Testing
Identify and mitigate security weaknesses through controlled simulations

Cloud Security
Protect your cloud resources, data, and applications to safeguard your business